Running a business is no easy feat. Succeeding involves overseeing many initiatives and facing many challenges on many fronts. In short: you have a lot going on. When it comes to the overall health of your business, managing your IT network should never be the straw that broke the camel’s back. Unfortunately, that’s exactly how it can feel for a lot of business owners and employees. Managing your IT network is a full-time job (sometimes many) and you already have a full-time job. In this eBook, we will illuminate the many reasons for foregoing self-management of your IT network in favor of partnering with a managed services provider to meet your technology goals.
There’s a lot for you to manage. Try managed services.
Surgeons perform surgery, accountants handle our taxes, and pediatricians take care of our children. No matter what kind of business you have, chances are that you’d rather focus on your actual business than the intricacies of running a modern IT network. So, who do you turn to when it comes to properly running your network? That would be a managed services provider (MSP). A managed services provider is any company that performs a contract service associated with your network or your infrastructure. While the specific services offered will vary from provider to provider, there are a few that we believe are most valuable, including:

Cybersecurity
One of the most essential managed services offerings is a full-scale and, most importantly, ongoing cybersecurity plan. The best cybersecurity solutions will address all the modern threats to your network, including cyberattacks, insider threats, and user error, as well as helping you keep up with the frequent changes and advances in network technology and malware.
Backup
In the USA, approximately 140,000 hard drives fail every week. If your personal computer or main server stopped working today, how much of your data would survive? If your machine crashes, or if you are hit by a cyberattack that compromises your data, you want to make sure that everything you’ve worked on can be retrieved from a secure location. To do this, make sure to speak with your MSP about a data backup plan.
Disaster Recovery
If disaster strikes, you need to have a plan in place to not only survive but continue to thrive. A recent example is the onslaught of hurricanes that impacted the Gulf Coast in 2017. Many businesses went under because they were unprepared to continue business in the face of a natural disaster. A disaster recovery plan is something you and your MSP design together to function as a guide for recovering your data and network systems to continue working outside of your normal operations.

Helpdesk
No matter how reliably or smoothly your network runs even in normal working conditions, issues will still pop up from time to time. Your employees can be more productive when they are able to quickly solve IT issues. For this reason, we suggest utilizing a 24/7/365 helpdesk. The helpdesk is particularly beneficial when you consider that many industries and key roles are becoming increasingly mobile, working extended office hours from a variety of devices and locations. Working with a dedicated helpdesk means you can benefit from a larger pool of expertise and assistance at any time.

Network Monitoring
The pinnacle of managed services for your business involves a hybrid of network monitoring and remote services. While the help desk ensures that your employees can quickly solve problems on their end, network monitoring provides a 24/7/365 overview of your network from the inside out. With network monitoring, technicians on your MSP’s team can not only maintain a real-time view of any possible intrusions, threats, or other network anomalies but also complete steps to mitigate and resolve issues as they arise.
Which managed services do you need?
The secret to choosing the right MSP for your business is in identifying the areas that need improvement and finding an MSP that provides a managed services package that fits those needs.
Guard your business with managed cybersecurity.
A cookie-cutter virus protection program just won’t suffice in a world where cybercrime is projected to cost $6 trillion annually by 2021. The attacks are coming. When they find your network, you want to be ready. $6,000,000,000,000,000 is an astronomical number and it can be hard to picture what that means to the average business. Let’s zoom in.
Cybersecurity is one of the most important services provided by MSPs. Rather than a one-size-fits-all approach, an experienced MSP’s approach to cybersecurity involves analyzing your strengths and weaknesses and maintaining complete and constant oversight of your network security. From creating best practices for your employees to implementing important software and maintaining patches and updates, your network is never safer than under the watchful eye of a managed services provider. The best cybersecurity solutions should address all types of threats. Here are the ones we find most common:
1. Sneak attacks
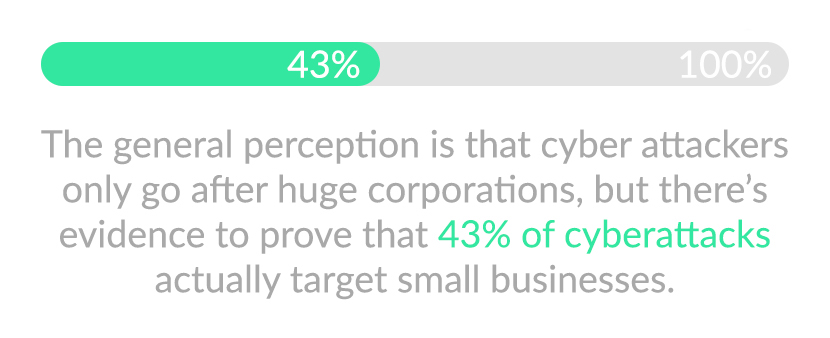
Your business should maintain a constant defense against cyberattacks. Modern cyberattacks are increasingly clever, relentless and evolving, and cybercriminals exercise an unprecedented lack of prejudice – they target anyone and everyone.
There’s sometimes no escaping the attacks, but there can still be preparation and fortification to minimize the effect. With so many types of sneaky cyberattacks, here are two you can recognize and avoid:
Phishing
You’ve probably had this happen before… You type in the URL for a website and the site opens but looks slightly different than the homepage you access most other days. The resulting page is asking not just for your username and password but also for other personal information like your credit card number or social security number to “verify your account.” If you’re a real quick-draw, you’ll wonder about the extra requests, check the URL and notice that you entered the wrong address. This cyberattack called phishing involves intruders pretending to be a trusted entity in an attempt to steal your personal information. They rely on their victims to be in a hurry, unobservant and willing to share far too much.
Malware
Downloading malware is as simple as opening an unknown attachment from an unfamiliar or questionable email. Something as simple as “You’ve won a free coffee, download certificate here” can turn anticipation and excitement into a compromised network. Malware can release unwanted code into your network, consuming your computer’s processing power and causing programs, or even the entire system, to crash. This is why we stress user education and training. It’s not enough to say never open an attachment from an email address you don’t recognize. Even a seemingly familiar sender can turn out to be a phony. Helping users become more vigilant is the key – including watching for suspiciously named attachments or URLs, plus emails using bad grammar, misspellings, incorrect personal references, or even incorrect information in the company footer or signoff.
2. Ransomware
Think of how this scenario would ruin your morning: You open your browser or desktop program and a message pops up: “Pay us $1,077 or we will delete the information on your computer/server.” $1,077 is the average amount of money lost per ransom attack. And these attacks are very common.
Avoiding ransomware is tricky. This type of malware can be delivered through emails, fake ads and malicious websites. It leaves behind code that blocks user access to the machine and demands payment to restore control and release data. Besides training your team to recognize the risky situations, extra tools can help with filtering and monitoring network and email traffic and unsafe URLs. It’s critical to remain aware of new and more convincing approaches emerging all the time. Ask your MSP to detail a plan for analyzing and safeguarding your network against cyberattack vulnerabilities.
3. Insider threats
You might be asking, “Where do all of these attacks come from?” Well, some are from malicious outsiders seeking to cause financial harm to your business and make an easy buck. Others are from within your own ranks.
Of that number, three-quarters were intentional and only one-quarter were accidental – meaning 45% of all cyberattacks are perpetrated by malicious employees. Your MSP should be able to work with your team to minimize insider threats with network checks and balances that involve access control, device registration, network monitoring, and assigning roles and permissions only to valid individuals.
Why Cybersecurity as a managed service?
With attacks coming in more variety and greater frequency, cybersecurity as a managed service is more important than ever for protecting your mission-critical business network. Partnering with professionals ensures your team gets the consistent, comprehensive and expert attention and protection to unify your cybersecurity efforts across channels, devices, users and systems.
Plan your backup to weather the unexpected storms.
With professional network monitoring and a solid cybersecurity plan that evolves with the times, your MSP will help you drastically reduce the chance of significant setbacks for your network. Even so, disasters do happen – and usually without much warning. The secret to surviving the unexpected or worst-case scenario is a backup and disaster recovery plan. A backup and disaster recovery (BDR) plan is a practical guide to maintaining the integrity of your network and restoring its operation in the face of critical failures. The ideal BDR plan will include a hybrid of preventative measures and practices that will secure and replicate your key systems and data, along with action points to focus on at the time of the disaster. Of course, your first questions might be, “Why bother? What are the chances that I will really need this?”
Data loss dangers
A recent industry report found that only 51% of business users back up their data to on-premises computers or external drives, and only 35% back up their data to the cloud. Almost a third of organizations surveyed don’t perform daily backups of their data. And worse, more than two-thirds don’t back up critical customer data. Ignoring the risk of data loss is dangerously negligent for business. A study by Verizon found that a small data breach where only 100 records are lost would most likely cost an organization between $18,120 and $35,730 – but as much as $555,660. Besides the potentially fatal financial loss for businesses, data loss creates a breach of trust that can also contribute to the loss of client relationships.
You get the point: Data loss is bad news. So, what causes data loss? Usually, data loss happens because of one of the following reasons:
Hardware failure
Computers aren’t built to last forever. They will all eventually break down. And that’s okay. As long as you don’t lose data when your computer shuffles off to the ethernet in the sky. Working to regularly copy your data to redundant physical servers, cloud servers will give you peace of mind that you can meet customer demands and regulatory standards like HIPAA standards.
Human error
If you haven’t had one of those “Did I just completely destroy my computer?” moments, consider yourself very fortunate.
Human error – a mistake as simple as spilling coffee on a server, clicking the wrong setting, or dropping a laptop down a flight of stairs (it happens!) – accounts for a massive amount of data loss. So, it pays to be prepared for the show to go on.
Natural disasters
Hurricanes, tornadoes, earthquakes, and related electrical storms, floods and fires, can all have a catastrophic impact on your business. If you don’t back up your data, you’ll lose more than just your physical property, you’ll lose vital customer information, operational files, and the ability to serve your customers. The truth is, data backup not only saves you from unwanted downtime, it keeps you running. Ultimately, you can think of BDR as a parachute. You wouldn’t jump out of a plane without making sure you have one, would you?
About Disaster Recovery
Once you have a plan to make sure all the right data is backed up for a rainy (or coffee-covered) day, you want to deal with the network operation issues surrounding a disaster. That’s when a disaster recovery plan becomes priceless. The recovery aspect of BDR will cover everything from the steps to relocating your network to accessing your data offsite backups to activating the services you will need from vendors supporting you in the continuation of IT operations. To survive and thrive after any disaster, you need to be able to get back to business as soon as possible. The disaster recovery plan will contain delegation of key IT recovery functions, a mandatory checklist, and security protocols to guarantee your employee and customer data is safe. Just like data backup, your recovery plan will have to adhere to both your professional standards and industry standards. Make sure to trust an MSP that has knowledge of your industry.
Your helpdesk keeps your network healthy.
The ideal goal of managed services is to create a network that minimizes the occurrence of significant IT incidents. Since we’ve established that many IT incidents are due to user error, addressing user IT issues is critical to maintain a functional network for your business. So, the best reason for having a helpdesk is explained by Murphy’s Law: Anything that can go wrong will go wrong. And that’s okay. The important thing is to have procedures and experts in place to handle issues as they arise. Notice that the key words there are as they arise. Your business operates in real time. Which means every minute, hour and day that an issue isn’t resolved is just more time that your employees can’t complete their work. A helpdesk will take care of those issues on the spot. What types of user support can a helpdesk provide?

Example 1: Weekend access
Dr. Rivera is a general physician working from a secondary office over the weekend. While attempting to access patient records for an upcoming appointment, he notices that the network has locked out his laptop and he doesn’t have the correct network password. Solution: Dr. Rivera contacts their 24/7/365 helpdesk and they are able to securely verify his identity and reset his password. His preparation is completed, and the appointment goes on as scheduled.

Example 2: Bandwidth barriers
Kit Harlowe is home health provider. She is completing a regular patient visit with updates to their charts and treatment plan, when the internet speed suddenly slows to a crawl. Solution: Kit contacts her managed helpdesk and they are able to walk her through the settings to run a network diagnostic. Through remote services, the helpdesk technician realizes she has downloaded a computer worm that’s sending an overflow of traffic to the network. They filter out the false traffic, which gets the network running faster and keeps Kit working.
In both examples, we address some of the most common reasons businesses choose to incorporate a helpdesk into their managed services
Flexible
Incidents and errors don’t clock in at 8 a.m. and leave at 5 p.m. They show up all the time, anytime, killing your team’s productivity. The only way to help your employees handle issues during their working hours is to have a knowledgeable team on hand.
Mobile-friendly
For many businesses, it has become imperative for employers to accommodate a workforce that has become both more mobile and more reliant on a variety of devices.
When your team is working on their own devices, they need someone who not only knows their network but has knowledge of these individual platforms.
Experienced and knowledgeable
When you have an entire helpdesk team working for you, you benefit from the combined knowledge of multiple technicians. Now consider all the other services we have spoken about. Who could possibly understand the intricacies of your network better than the team who builds them every day? Whether your team is facing normal issues in day-to-day operations or the more complicated incidents that crop up in the evolving mobile workplace, you can count on a helpdesk to provide superior and timely solutions.
We really enjoy chatting about ways to improve your network.
With expertise and experience in all of the above-managed services, RWA will work to build a custom solution that fits your specifics business needs. Contact us at your earliest convenience and we’ll share as much info about the above-managed services as you’d like.