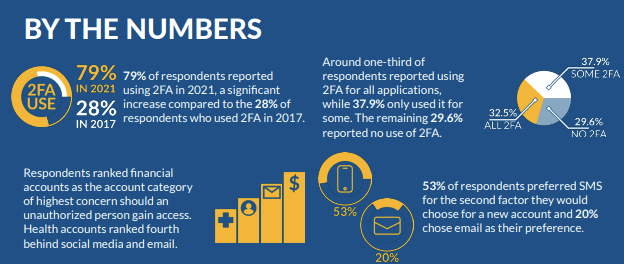
The healthcare sector experiences twice as many cyberattacks as any other industry. Still, healthcare professionals invest less than 6% of their budgets in cybersecurity.
If you are a medical professional, now’s as good a time as any to beef up your security efforts. As a result, you can safeguard patient data and prevent hackers from stealing sensitive information. Here are some healthcare security threats to look out for in 2023.
Phishing attacks
Use of e-mail in medicine has only grown over the past decade, and phishing attacks continue to escalate. This type of security threats starts when a healthcare clicks on an infected email. Once this malware infiltrates a computer system, it can access valuable files and folders.
“The attacker can then use this software to gain access to the healthcare organization’s financial, administrative and clinical information systems,” says Tech Crunch.
Phishing attacks can have a detrimental impact on a hospital or medical practice. Malware often renders computer systems unusable, which has a significant impact on patient safety. In this scenario, doctors and nurses are unable to access important records. In turn, this can put organizations in big trouble in terms of compliance and liability lawsuits. And, in rare cases, it can even put patients’ lives at risk.
These type of attacks greatly increase the chances of hackers stealing valuable data.
Old legacy systems and networks
Old computers and networks could increase security vulnerabilities. As you may expect, Legacy systems may not function as efficiently as newer ones, and they often lack the latest security patches and updates.
“Healthcare is vulnerable due to historic lack of investment in cybersecurity, vulnerabilities in existing technology and staff behavior,” says Science Direct.
Even if medical organizations lack the money to invest in brand new technology, they should take steps to improve their network security. Installing the latest security software and a firewall, for example, and getting rid of old programs could prevent data from being stolen, increase compliance and increase patient trust.
Staff misuse
Insider misuse makes up 15% of all security breach incidents. Usually, this involves medical employees gaining unauthorized access to sensitive data and sharing it with other people.
“Surprisingly, the reason insider misuse stands out in the healthcare industry is because of the amount of people who get jobs in the industry for the sole purpose of infiltrating the system and gaining access to patient health information,” says the University of Illinois at Chicago.
Encrypting valuable data and setting up access controls — where only certain members of staff can access information. This could help to reduce this problem.
Ransomware
Ransomware is one of the biggest security threats in healthcare right now. In May 2017, a ransomware attack called WannaCry targeted computers running the Microsoft Windows operating system and had an impact on Britain’s National Health Service — the biggest single-payer healthcare system in the world.
A similar ransomware attack on your organization could spell disaster. Once ransomware infects your computer, you will probably be unable to access files and patient records unless you pay cybercriminals a ransom.
These are just some of the security threats you need to avoid if you work in the healthcare sector. However, working with a professional who takes care of your security defense needs will reduce phishing attacks, ransomware, staff misuse and old legacy systems from malfunctioning.