5 signs you’re ready for an IT update
Choosing the right technology for your business is all about striking the right balance. While you don’t want to hastily jump on the bandwagon every time a shiny new gadget comes along, you also don’t want to miss the boat and fall behind your competitors.
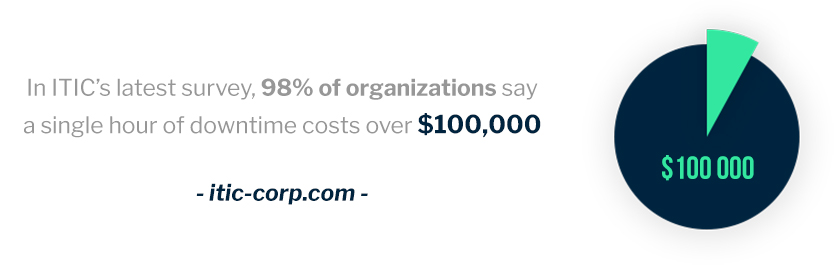
Unfortunately, many companies are too cautious for their own good when it comes to updating their IT systems and processes. According to a 2016 survey, U.S. organizations are losing up to $1.8 trillion in wasted productivity every year due to outdated technology. What’s worse is that 37% of employees believe their company is using outdated business tech — which can easily lead to morale issues.
The fact that you’re even wondering if you should upgrade your IT systems is a surefire indicator that it’s time for an IT update. Below, we’ll discuss five signs that prove your company is in need of a technological facelift.
Collaboration issues
In theory, collaboration sounds like the solution to all your company’s problems. Unless it’s done right, however, collaboration can often create just as many issues as it solves.
Efficiently managing tasks and files among all members of a team are two of the greatest challenges for collaboration:
- Without well-defined rules for sending updates and asking questions, team members might communicate across half a dozen different channels — from email and team hubs to phone calls and instant messages.
- Keeping track of different file versions and edits can be extremely difficult, especially when using different channels as described above.
In the absence of a dedicated person to serve in the role of project manager, many companies use project management software such as JIRA, Trello and Asana. These applications allow users to assign each other tasks, set deadlines, track progress, and streamline communication. It’s a simple update that can have a huge impact on your business.
Security vulnerabilities
The older your legacy IT systems are, the easier it is for malicious actors to find and exploit flaws in them, exposing your network to data breaches and other cyber attacks.
For example, the WannaCry malware, which took the cybersecurity world by storm in 2017, was able to spread so quickly because it took advantage of weaknesses in older Windows operating systems.
However, the cloud might be the fix to this problem.
In fact, more than 90 percent of U.S. companies already use cloud computing in some fashion. Of those organizations, 64 percent agree that cloud infrastructure is “more secure” than legacy IT systems. This is partly because the cloud pushes out updates automatically — which means you’ll always have access to the latest security patches and bug fixes.
Poor customer service
Whether you’re a mom-and-pop e-commerce site or a massive B2B firm, your customers are the lifeblood of your business. Having employees complain about your aging technology is one thing, but having clients complain about it is a clear sign that things need to change.
If you take your customer service seriously, then it’s time to adopt a software solution for customer relationship management (CRM). CRM applications help you manage your leads, your interactions with customers, and your relationships with clients and vendors.
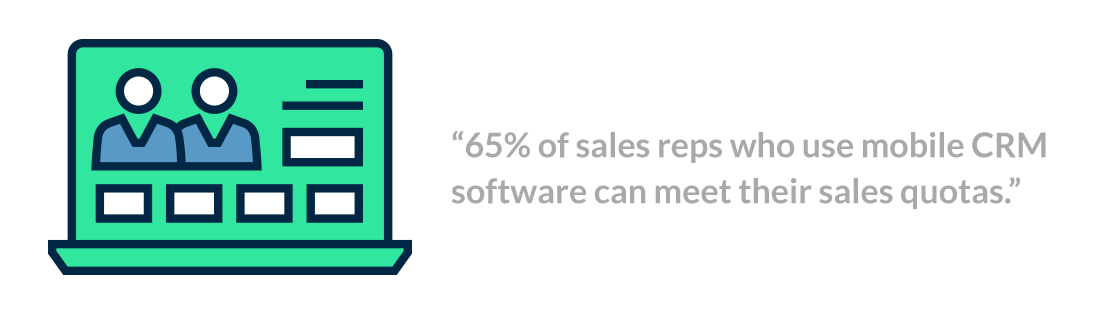
Eighty-seven percent of companies using CRM software are using cloud-based CRM — enabling employees to access the application from devices like their personal smartphones and tablets. While 65 percent of sales reps who use mobile CRM software can meet their sales quotas, only 22 percent of sales reps who use non-mobile CRM software can say the same.
Failure to deliver
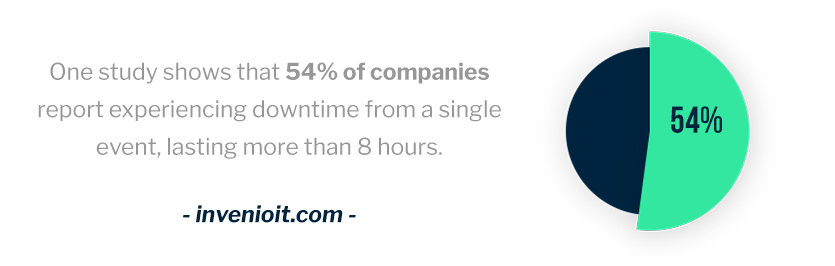
If left to grow unchecked, legacy IT issues can affect your bottom line in more ways than one and lead to negative consequences such as missed deadlines or service downtime. These types of problems can happen for any number of reasons — for example, obsolete hardware or website hosting plans that don’t offer enough wiggle room.
As soon as these internal problems start to turn into external problems, it should be a clear wake-up call — your IT infrastructure as a whole needs to be rethought.
To make matters worse … if you don’t keep your entire system up-to-date, software and hardware compatibility issues can prevent you from installing the solutions you need to take your business to the next level.
Rapid growth
On a more positive note, startups and small businesses experiencing periods of rapid growth also have reason to upgrade their technology stack.
Your original software and servers might have been perfect for your needs when you had three people working out of your garage — but now that you’re at 30 people and growing, your old tech is no longer sufficient.
At regular intervals, you should do a sanity check of your existing applications and systems to make sure they’re still working well for your purposes. Early-stage startups should choose solutions that are scalable and can grow alongside them in the future.
Clearly, technology is important. But where to start … now that’s not so clear. To get you headed in the right direction, check out 4 IT consulting projects that are guaranteed to make your business better.











 Whether your business currently utilizes a managed service provider (MSP) or you are working your way up to a full-scale IT solution, you will often find yourself in need of professional services. IT consulting becomes handy when you are dealing with the type of projects that don’t require monthly maintenance, but still require professional assistance.
Whether your business currently utilizes a managed service provider (MSP) or you are working your way up to a full-scale IT solution, you will often find yourself in need of professional services. IT consulting becomes handy when you are dealing with the type of projects that don’t require monthly maintenance, but still require professional assistance.